Generating Public Private Dsa Key Pair
- Generating Public Private Rsa Key Pair Windows
- Generating Public Private Dsa Key Pair Chart
- Generating Public Private Dsa Key Pair Meaning
How to Generate a Public/Private KeyPair for Use With Solaris Secure Shell

When you delete a key pair, you are only deleting the Amazon EC2 copy of the public key. Deleting a key pair doesn't affect the private key on your computer or the public key on any instances that already launched using that key pair. Generating a Secure Shell (SSH) Public/Private Key Pair Several tools exist to generate SSH public/private key pairs. The following sections show how to generate an SSH key pair on UNIX, UNIX-like and Windows platforms. Nov 10, 2011 Your public and private SSH key should now be generated. Open the file manager and navigate to the.ssh directory. You should see two files: idrsa and idrsa.pub. To generate a DSA key pair for version 2 of the SSH protocol, follow these steps: Generate a DSA key pair by typing the following at a shell prompt: $ ssh-keygen -t dsa Generating public/private dsa key pair. Asymmetric cryptography also known as public-key encryption uses a public/private key pair to encrypt and decrypt data. Public key in asymmetric cryptography is available to public but the private key must be protected with the user, else it can be used to decrypt data. The public and private keys are known as a key pair. Public key cryptography enables you to securely access your instances using a private key instead of a password. When you launch an instance, you specify the key pair.
Users must generate a public/private key pair when their site implementshost-based authentication or user public-key authentication. For additionaloptions, see the ssh-keygen(1) manpage.
Before You Begin
Determine from your system administrator if host-based authenticationis configured.
Start the key generation program.
where -t is the type of algorithm, one of rsa, dsa, or rsa1.
Specify the path to the file that will hold the key.
Bydefault, the file name id_rsa, which represents an RSAv2 key, appears in parentheses. You can select this file by pressing the Return key. Or, you can type an alternative file name.
Monster hunter generations ultimate story key quests. Tier 1BASE: Culldrone and Mauldrone. Ordering Jelly from either cat Trader also can occasionally yields Larval Extract as well. Below is the full set of Kinsects you can aim for and the mats you need to level up your bug based on the official Japanese Monster Hunter X guidebook. Level 2: Huskberry x3, Worm x3. Once you’ve fed a Kinsect enough, all the Jelly items get grayed out and you can now upgrade the Kinsect itself.Depending on your level and which stats you invest in, you can evolve your Kinsect into different insects.
The file name of the public key is created automatically by appendingthe string .pub to the name of the private key file.
Type a passphrase for using your key.
This passphraseis used for encrypting your private key. A null entry is stronglydiscouraged. Note that the passphrase is not displayed when youtype it in.
Retype the passphrase to confirm it.
Check the results.
Check that the path to the keyfile is correct.
At this point, you have created a public/private key pair.
Choose the appropriate option:
If your administrator has configuredhost-based authentication, you might need to copy the local host's publickey to the remote host.
You can now log in to the remote host.For details, see How to Log In to a Remote Host With Solaris Secure Shell.
Type the command on one line with no backslash.
When you are prompted, supply your login password.
If your site uses user authentication with public keys, populateyour authorized_keys file on the remote host.
Copy your public key to the remote host.
Type thecommand on one line with no backslash.
When you are prompted, supply your login password.
Whenthe file is copied, the message “Key copied” is displayed.
(Optional) Reduce the prompting for passphrases.
For a procedure, see How to Reduce Password Prompts in Solaris Secure Shell. For more information, see the ssh-agent(1) and ssh-add(1) man pages.
Generating Public Private Rsa Key Pair Windows
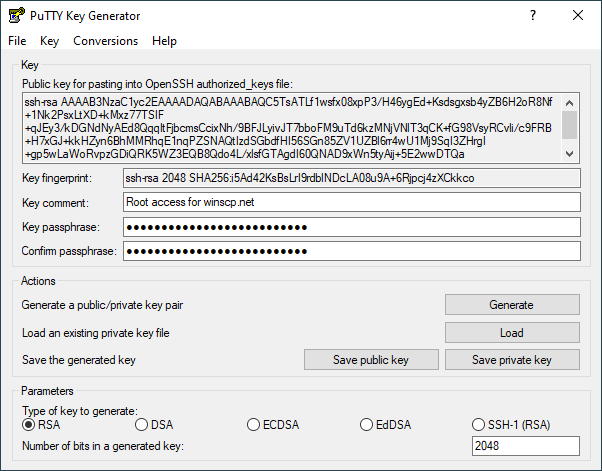
Generating Public Private Dsa Key Pair Chart
Example 19–2 Establishing a v1 RSA Key for a User
In the following example, the user cancontact hosts that run v1 of the Solaris Secure Shell protocol. To be authenticated by v1hosts, the user creates a v1 key, then copies the public key portion to theremote host.