Aws Kms Generate Data Key
- Aws Kms Generate Data Key In Windows 10
- Aws Kms Generate Key
- Aws Cli Kms Generate Data Key
- Aws Kms Generate Data Key West
- Aws Kms Key Rotation
Step 2- Generate the data key. Next, we ask AWS KMS to generate a data key referencing a CMK. The CMK is referenced to encrypt the data key. We will use the CMK created with our key material, this is the material we imported, key alias is 'ImportedCMK'. Use the following command to generate a symmetric data key with 256 bits length encrypted. General AWS KMS Concepts. AWS Key Management Store (KMS) is a managed service that enables you to easily encrypt your data. AWS KMS provides a highly available key storage, management, and auditing solution for you to encrypt data within your own applications and control the encryption of stored data across AWS services.
Encryption is an integral part of the AWS KMS operations and its interactions with other AWS services. In this section we are going to get a better understanding of it and make some hands-on practices. AWS KMS mostly uses envelope encryption, but can also encrypt data directly without envelope encrytion.
Envelope encryption is the main encryption vehicle for AWS services using AWS KMS.
The section is divided in the following parts:
How Envelope Encryption works in practice
AWS KMS is able to encrypt and decrypt up to 4 kilobytes (4096 bytes) of data. With other volumes of data, normally you will use a data key to perform encryption operations outside KMS through envelope encryption.Envelope encryption refers to the practice of protecting the data by encrypting it with a data key, and encrypting the data key itself with another encryption key, a CMK under KMS in this case.See the following figure from AWS KMS documentation.
<Figure-1>
AWS KMS is also capable of generating data keys to encrypt data from CMKs.NOTE: Data keys are only generated by AWS KMS, not stored or used to encrypt by AWS KMS itself.
Data keys are very different from a CMK, which never leaves AWS KMS and is only used in memory. Besides, data keys can be obtained in plain text or encrypted.
Once the data is encrypted and stored with a data key, the data key is stored encrypted with the data itself, while the plaintext version of the data key is deleted (for security best practices).
Therefore, to decrypt the data, the CMK needs to decrypt the encrypted data key and then, with the data key in plain text, the decrypt operation can take place.This adds a tier of protection to your data and better manageability. If a data key is compromised, only the service or data using that particular data key is compromised, no other data. If only one key was used for all data encryption across the platform and it gets compromised, the whole platform data would be also compromised.
Let's see envelope encryption in action with AWS KMS.
Step 1 - Create the secret text
First thing we will do is to create a file with the data we want to encrypt under envelop encryption. A sample 'secret' text file in this case with the text 'Sample Secret Text to Encrypt'.
Step 2- Generate the data key
Next, we ask AWS KMS to generate a data key referencing a CMK. The CMK is referenced to encrypt the data key. We will use the CMK created with our key material, this is the material we imported, key alias is 'ImportedCMK'. Use the following command to generate a symmetric data key with 256 bits length encrypted with our CMK.
You will notice that the command will fail to run. Our current Role with Power User permissions does not have enough privileges to generate a data key. As per least privilege best practices, we are providing permissions as needed in policies attached to the role that can be easily tracked and detached when such permission for that user is not needed any more.
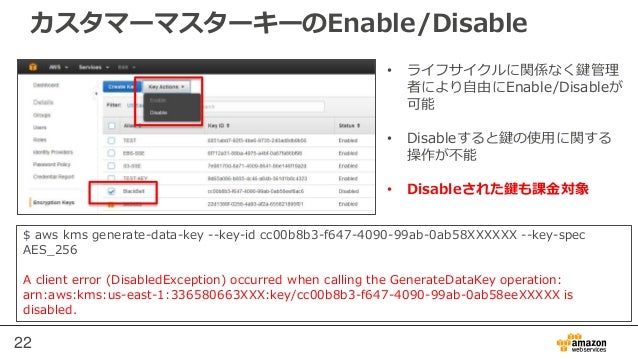
We need to provide with permission to generate a data key.
The process is the same as we have seen twice in the previous section of the workshop, please go back to it if you need to in the following link: 'Create the import material and encrypt it for the import'
Basically, you need to go back to the AWS console, in the services area navigate to IAM and go to 'Policies'. We are going to create a new policy and attach it to the Power user role.
As we did in the previous section, click on new 'Create Policy', Select KMS as the service, go to the Actions area.In the 'Write' section, select 'GenerateDataKey' operation. Additionally select 'Encrypt', 'Decrypt' and the tagging operations as you can see in image below, we will need them for the nexts steps. and 'Any' as resource.
<Figure-1>
Click on 'Review Policy' and then give the policy a name, for example 'KMSWorkshop-AdditionalPermissions'.
You can click now in 'Create Policy'. Once created, attach it to the role KMSWorkshop-InstanceInitRole.
Once the policy is attached, if you try the same command again, it will succeed now. The command will return a JSON output with:
- the plaintext data key - Plaintext key in b64 encoding
- the KeyId used to encrypt plaintext data key
- A CiphertextBlob which is the encrypted data key generated, in base64 enconding.
Write these values down, we are going to needed them shortly.
Please note the command used a new parameter: 'encryption-context'. This is an optional key-pair value that provides additional context about the data and that needs to be provided as well when decrypting the data. This is because, when provided, it is bound to the cryptographic operation.
Encryption Context, besides helping with the integrity of the encrypted data, it has many other uses. For example: use it to set policies, to provide Grants or to monitor encrypt/decrypt operations in CloudTrail (will see later in this section).See additional information about encryption context in this part of the AWS KMS documentation.
Step 3 - Encrypt the secret text
We have now a data key 256 bit length that we can use to encrypt. We can use any encryption tool or library with the data key we have created to encrypt our data. ** Remember that AWS KMS does not store or use the data key for encryption **.
Let's use OpenSSL library to encrypt the sample file we want to be secret with our newly created data key.
We need to decode the plaintext data key we obtained above (Plaintext), as it is in b64, and store it in a file.
Use a command like the one below, where the argument for 'echo' command is the plaintext key obtained when creating data key. The output file name will be datakeyPlainText.txt.
Apr 10, 2020 To get an API key: Go to the Google Cloud Platform Console. Click the project drop-down and select or create the project for which you want to add an API key. Click the menu button and select APIs & Services Credentials. On the Credentials page, click Create credentials API key.  For this navigate to TranslatePress- Settings, and make sure to Enable Automatic Translation, by setting it to Yes.Then, under Translation Engine, select Google Translate v2. This will uncover the Google Translate API key field. Place the API key in this field and Save Changes. You can now simply navigate to the front-end of your website and browse it in the language of your.
For this navigate to TranslatePress- Settings, and make sure to Enable Automatic Translation, by setting it to Yes.Then, under Translation Engine, select Google Translate v2. This will uncover the Google Translate API key field. Place the API key in this field and Save Changes. You can now simply navigate to the front-end of your website and browse it in the language of your.
We wil do the same for the encrypted plaintext (the CipherTextBlob) we have obtained when creating data key. Therefore, the argument for 'echo' command is the CipherTextBlob value of the data key genetarion's JSON output. We wil save it and save it in a file name datakeyEncrypted.txt:
Now we are ready to encrypt the file with the text we want to keep secret. Remember we stored the text in the file samplesecret.txt. For the job, we will use the OpenSSL library again, encrypting with AES256:
This command encrypts in AES256 bits the input file 'samplesecret.txt', with the data key in Plaintext stored in file 'datakeyPlainText.txt' and saves the encrypted output to file 'encryptedSecret.txt'.We have our text now encrypted in the file encryptedSecret.txt. You can do a 'more' or 'cat' operation over it. You will notice the encryption. The original text is not recognizable.
Following envelope encryption best practices, you will now store the file encrypted with the encrypted data key and delete the plaintext key, avoiding getting it compromised.
Step 4 - Decrypt the encrypted secret text
If we want now to reverse the operation and decrypt the secret text stored in encryptedSecret.txt, it will be a 2 steps procedure.Remember that we don´t have the data key in plaintext to be used for decryption, we have removed it for security best practices.
We have the data key encrypted that was provided to us when calling the AWS KMS generate data key operation and that we stored as b64 decoded in file datakeyEncrypted.txt.
Therefore, the first step is to decrypt the data key with the appropriate Master Key (CMK) that was used to encrypt it. In this case we will use the command aws decrypt (see full reference in this part of documentation). This command will tell AWS KMS to revert the encryption made over the data key.
Note: We don´t need to provide the KeyId that was used to encrypt the data key, the encrypted data contains metadata to provide this information to AWS KMS.
The command will fail because when we generated the data key in plaintext and encrypted it with our CMK in the step 2, we used an encryption context.This encryption context was used in the encryption operation of the plaintext data key, this is: to produce the encrypted data key (the CiphertextBlob). Therefore we need to provide the encryption context to be able to decrypt correctly:
Great! As you can see, the output of the command has the data key in Plaintext. We had removed it and only stored it encrypted, but with AWS KMS and the appropriate CMK, we have it back.
We need now to decode it from base64 and use it to decrypt the encrypted secret file, encryptedSecret.txt. Again using the OpenSSL library: Copy the plaintext key and use it as an input to 'echo', as you can see below.
Now that we have the data key in Plaintext and decoded from base64, let's decrypt:
Good job, we have the secret text 'Sample Secret Text to Encrypt' decrypted.The data to be encrypted and decrypted by your applications would use envelope encryption in a similar way. It is a powerful mechanism, enabled by AWS KMS CMKs, to protect in two tiers, the integrity and confidentiality of your data.
By completing this part of the workshop you now have a better understanding of what envelope ecnryption is, let's now see how it applies for AWS services working with AWS KMS.
Envelope encryption. Server side encryption
In AWS there are main two main procedures to protect your data at rest: Client Side Encryption (CSE) and Server Side Encryption (SSE).
For example in Amazon S3, you can encrypt your data before uploading it into the Amazon S3 Service (client side encryption) or encrypt once the data is there (server side encryption). More details in this link to the S3 documentation. A similar approach can be taken in other services like Amazon DynamoDB, see details here.
The envelope encryption mechanism just described in previous section is the mechanism behind the Server Side Encryption that takes place in the AWS services that use AWS KMS. There are very good descriptions on how AWS KMS is being used by different AWS services in this part of the AWS KMS documentation here.
Aws Kms Generate Data Key In Windows 10
For the workshop, let's see an example of attaching a disk to our working instance. We will encrypt it with AWS KMS and the CMK we have created importing our key material, its alias was 'ImportedCMK'.
We start by going into the AWS console. Navigate to Amazon EC2 service. Look in the left pane. Locate 'Elastic Block Store' and click on 'Volumes'.
<Figure-2>
Now in the upper area, you can click on 'Create VolumeNikon capture nx2 windows 10. ' to create a new Amazon EBS disk. Once in the volume creation screen, and for the workshorp, you can leave the defaults in most fields- Except for the following: Ensure you have selected the same 'Availability zone' as your EC2 instance is running on (It is easy to find out: you can look into the EC2 service, Instances area in the left pane, select your instance and locate the information 'Availability Zone' below). The disk can only be attached to instances in the same availability zone.
Ensure also that you have clicked the 'Encryption' checkbox. Then select the CMK you want to use from AWS KMS. Let's select the CMK that we have imported with our own key material, the alias was: ImportedCMK.
<Figure-3>
Create a tag for the volume, for example a key-pair like: Name: WorkshopEBS.Click on 'Create volume' at the right bottom of the screen. The volume will start being created and will be ready to be attached to the instance in a few seconds.
We have now a encrypted volume that can be attached to our instance.
In order to do so, navigating to EC2 service in the AWS console again, just go to the 'Volumes' in the left pane. Check Under 'Elastic Block Store' on the left are of the screen and select the volume you have created. Cick on the 'Actions' button and select 'Attach'. In the new window, select the instance we want it to be attached to.
Once the attachment process has finished, if you go back to the terminal connection to your instance, you can see the encrypted 100GiB disk is available for being mounted and used.
Behind the scenes, an envelope encryption process through AWS KMS has taken place:
Amazon EBS has requested AWS KMS to generate a data key under a CMK, 'ImportedCMK'. The encrypted data key is stored within the EBS volume metadata. When data needs to be stored (and therefore encrypted) in the EBS volume, Amazon EC2 ask AWS KMS to decrypt the encrypted data key that EBS has in the metadata. Amazon EC2 obtains the data key in Plaintext back from the operation with AWS KMS. Then, the data is encrypted with the Plaintext data key before being stored in EBS.
Furthermore, encryption context was used during the process to enforce the security and better traceability.The encryption context is used with the volume-id of the Amazon EBS volume in all the encryption and decryption operations.See more details in the following link to the Amazon EBS documentation.
Envelope encryption. Client side encryption
In the first topic of this section of the workshop (How Envelope Encryption works in practice) we have just seen an example of how AWS KMS can encrypt in client side by generating a data key, using an envelope encryption mechanism, to encrypt a secret text file with two tiers of protection.
Aws Kms Generate Key
While you can code all the primitives and commands to implement encryption on the client side, AWS has a SDK, the AWS Encryption SDK. This SDK uses envelope encryption and it is integrated with AWS KMS. It will implement most of the operations we have seen before as simple API calls. AWS KMS can become a Master Key provider for the AWS Encryption SDK, however you may use other Master Key provider with the SDK.
I recommend to take a look at the AWS Encryption SDK. Also, some AWS services have specific encryption SDKs, like the one in Amazon DynamoDB: the 'DynamoDB Encryption Client', you can take a look in this link.
Encryption using AWS KMS with no Data Key
You can also use a CMK in AWS KMS to encrypt and decrypt a secret directly, without the generation of a Data Key and hence, without the envelope encryption process. Remember, AWS KMS is able to encrypt and decrypt up to 4 kilobytes (4096 bytes) of data. We can use the CLI or APIs.
In this example, we will use the CLI to encrypt a secret and decrypt using the CMK itself. Note: this encryption operation takes place in AWS KMS itself.When a data key is generated via the CMK, the encryption and decryption process with that data key happens outside AWS KMS.
Let's Create a new secret file.
We are going to encrypt it with a CMK and use an encryption context that will need to be provided in the decrypt operation.
Aws Cli Kms Generate Data Key
Note we have called the CMK used to encrypt by its alias. The input file needs the 'fileb' prefix to be processed in binary, while the output is decoded from b64 to the new output file 'NewSecretsEncryptedFile.txt'
Take a look at the Encrypted file:
Aws Kms Generate Data Key West
Great, It unreadable as is encrypted. Can´t read the original text. Now let's decrypt it.
Wait, what is the problem?. At this point of the workshop, we should know that without the encryption context, the operation will not succeed. That was the problem. Let's try it again including the encryption context we stated during the encryption process:
If you now take a look at the file we have created with the previous command 'NewSecretsDecryptedFile.txt'. The secret text is now back unencrypted and ready for us.
Aws Kms Key Rotation
You have completed the second section of the workshop. In the next section we will work with a real-life Web App and will try to implement best practices. You can now navigate to the next section of the Workshop